API Security - Basics:
Everything You need To Know
Continuously discover and secure all APIs
APIs form the backbone of enterprise applications, comprising over 80% of all internet traffic. Yet, they are often the weakest link in cybersecurity. CISOs, DevOps, and IT Security teams face the daunting challenge of monitoring APIs for threats and vulnerabilities. With the increasing complexity and volume of APIs, traditional security measures fall short, leaving critical data and systems at risk.
- Why your APIs are not as secure as you think (white paper)
- Best practices for mitigating risks (white paper)
- Guide to securing the API attack surface (Research study from Enterprise Security Group)
- Top 5 API security myths - and what to do instead (20-min video)
- Graylog API Security (5-min demo)
- Install Graylog API Security Free Edition (download & install)
Understand the challenge
Tools such as Web Application Firewalls (WAF) and API Gateways focus on performance monitoring and controlling HTTP traffic.
They do not provide threat detection and response for APIs and cannot protect against authenticated attacks that bypass perimeter defenses.
Get the 2 white papers.
Organizations rate APIs as the element in the cloud-native stack most susceptible to attack, and attacks stemming from insecure APIs were the most commonly identified cybersecurity incident tied to cloud-native app development over the last 12 months. As the number of APIs continues to grow, security risk increases.
TechTarget’s Enterprise Strategy Group surveyed 397 IT, cybersecurity, and application development professionals at organizations in North America responsible for evaluating, purchasing, and managing API security solutions. You can learn more in this 31-page report by ESG Research.
Watch an overview video on the right now
Register and download the full guide here.
While awareness and attention towards cybersecurity are on the rise, some popular and persistent myths about cybersecurity have almost become threats themselves. API security requires a modern understanding of the threat landscape, with the context that most API providers desire to be more open and accessible to all. This video debunks the 5 worst myths about protecting your APIs. Watch the video
Video Key Takeaways:
-
- Myth 1: Attacks are Rare
- Myth 2: Attackers are Outsiders
- Myth 3: IP Addresses Represent Users
- Myth 4: Authentication and TLS are Sufficient
- Myth 5: Developers are Disinterested in Security
It’s a dedicated API threat monitoring solution. With it, you gain:
- API Discovery: Automatically discover and categorize all APIs, ensuring none stay under the radar
- Complete API Request and Response Detail Capture, creating a readily accessible datastore for attack detection to identify common threats and API failures swiftly and accurately
- Risk Assessment Scoring: Get an overall picture of your cyber risk and API vulnerabilities, enabling you to identify areas where you can strengthen your defenses
- Real-Time Threat Intelligence: Stay ahead of emerging threats with out-of-the-box threat signatures
- Remediation Tips: Once a threat is detected, Graylog API Security goes far beyond blocking IP addresses, automatically providing helpful, straightforward remediation information
- High-Level Insights presented on a summary dashboard to facilitate productive discussions across the company
🆓 Try it now!
⬇️ See it in action
What is included with Graylog API Security - Free Edition?
Graylog API Security - Free Edition is a self-managed private cloud / on-prem solution limited to 1 node and 16GB of local rolling storage (it does not include Iceberg connectivity). Once storage capacity is reached, old data is rolled off as new data comes in. The license key must be renewed annually. Limited to 1 license per company.
3 steps to get started
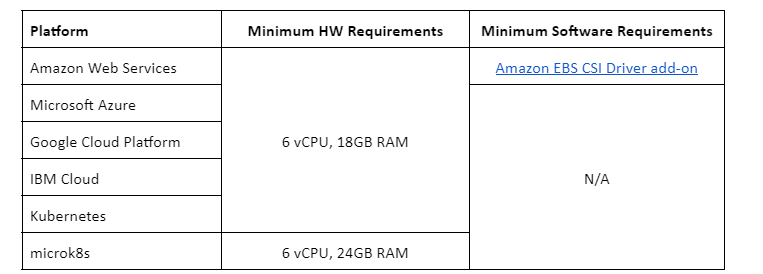
- Review the technical requirements below
- Use the Getting Started Guide for installation
- Fill in the form and instantly receive your license key
Need help obtaining your license key?
CONTACT US
Get Graylog API Security - Free Edition
Graylog API Security provides API threat detection and incident response capabilities that provide complete visibility into your environment, real-time monitoring for attacks, and thorough analysis of end-to-end API request and response data.