Graylog provides answers to your team’s security, application, and IT infrastructure questions by enabling you to combine, enrich, correlate, query, and visualize all your log data in one place.


Read the press release about a free version of Graylog API Security.
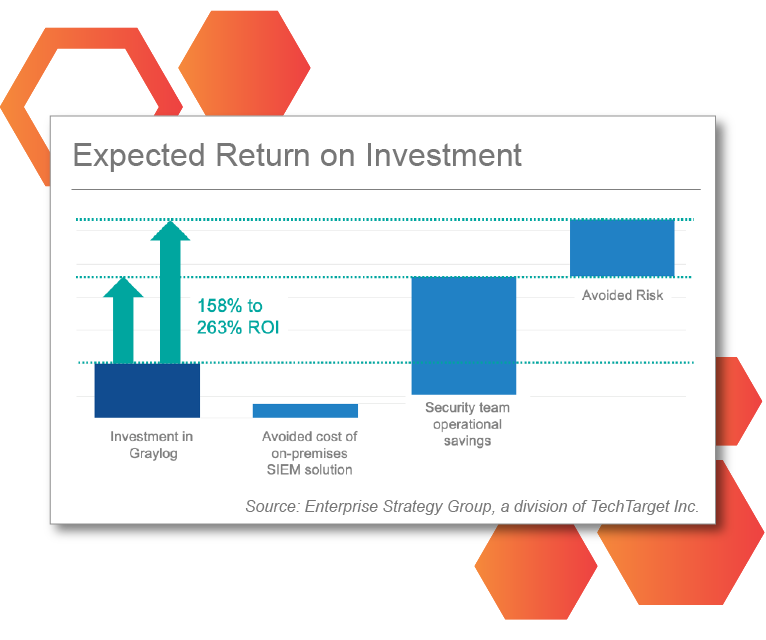
Read the full research report from Enterprise Strategy Group.
Register to learn the features and capabilities in Graylog 5.2
Search terabytes of data in milliseconds so you can ask more questions and get more answers. Save and share searches to save time and share expertise.
Combine a variety of data widgets to customize dashboards to exactly what you want to see. Then quickly drill-down and even launch saved searches.
Use triggers, aggregations and correlations to get alerts through SMS, Slack, PagerDuty, email, and more. Or kickoff a custom script for full creativity.
Work with the same widgets you use for search results and dashboards to easily build reports and automate their delivery to any email address.































Follow Us:
© 2024 Graylog, Inc. All rights reserved