On-demand Webinar
HOW GRAYLOG HELPs WITH PROACTIVE THREAT HUNTING CAPABILITIES
SEE EVERYTHING. BE READY FOR ANYTHING
View the Threat Hunting recorded webinar including a demo of log management capabilities and cybersecurity best practices by Graylog security experts.
When major cybersecurity incidents like the recent SolarWinds attack become public, the first question every cybersecurity person gets asked by their organizations is, “are we vulnerable?" Often this question is not as easy to answer as management would like it to be. There are Shadow IT concerns, questions about specific versions and patch levels, and analysis of compensating controls to be considered. However, indicators of compromise appear in the context of event logs.
Learn how Graylog log management system can help you with proactive threat hunting capabilities in this 30 minute recorded session including:
- Lessons learned from recent attacks
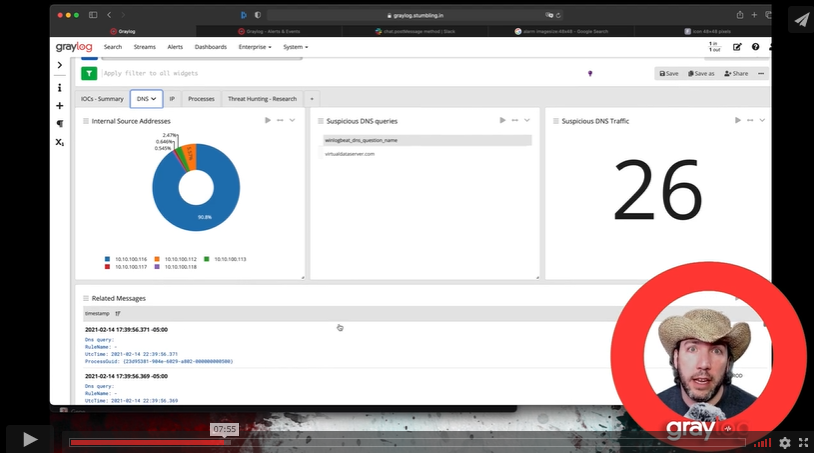
- Threat hunting for risky IOCs
- Malicious and anomalous activity detection
- Monitoring for threats with Alerts and Dashboards
Register and watch the Threat Hunting with Graylog on-demand webinar now.
THREAT HUNTING [On Demand Webinar]
SUPER FAST THREAT-HUNTING
Gather and aggregate incident data to proactively go looking for malware, hacks, phishing, and endpoint attacks. Explore your data without having a complete plan prior to engaging in the search.
Go beyond the simple drill-down—the power of Graylog’s integrated search, workflow, dashboards, and reports lies in its ability to expand and reveal more information as you go, delving deeper into the data to find the right answers.
WHAT WE DO
COMPREHENSIVE INCIDENT INVESTIGATION
Detect threats and breaches from across your business with correlated data visualization from all sources, organized into a single screen. With Graylog’s real-time information at your fingertips, you can pinpoint the source of your issues fast. A perfect addition to your cybersecurity toolkit, it prepares your team to proactively reduce risk before a small problem becomes a big one.
IDENTIFY MALICIOUS ACTIVITY
Find the real threats in massive amounts of data produced by firewall logs, applications, endpoint OSes, networking equipment, DNS requests. Identify issues like USB devices plugged into sensitive endpoints or installations of browser plug-ins with known vulnerabilities. With the right defenses in place, your security posture has never been so strong.
KNOW THE IMPACT
Trace the path of an incident to identify which systems, files, and data has been accessed through the log files. Marry log data with threat intelligence, HR systems, physical security systems, Active Directory, geolocation, and more to get additional insights and data visualizations.
FLEXIBILITY TO FIT YOUR SOC STACK
Enhance capabilities and strengthen security by combining SIEM and log management. Graylog lets you see availability and alerts immediately by visualizing metrics and trends in one central location so you can understand where and how a threat began, the path it took, what it impacted, and how to fix it. Maximum protection with minimum risk. Or if you use a centralized help desk system don’t need dedicated incident management ticketing capabilities, use Graylog as your SIEM!